Capture Raw Bluetooth LE Frames
When developing Bluetooth software or hardware, you often need to see the raw data communication between your application and a device. While Microsoft provides a Bluetooth Test Platform software for Windows, it offers very limited features and requires expensive hardware. That is where the CC2540 USB dongle comes in. This Bluetooth USB dongle can act as a BLE sniffer, providing an accessible and affordable solution. It is cheap and widely available.
A BLE sniffer (also known as a Bluetooth protocol analyzer) acts as a passive listening device that captures BLE packets sent over the air from various devices within the direct radio range. This is very helpful when you need to debug communication between devices without interfering with and affecting the communication between them. This tool is also very useful when you have a device with an unknown protocol and a mobile application. The sniffer helps to understand the device's protocol and to implement it in your application.
While the CSR dongle comes with its own software for capturing Bluetooth packets, deeper tasks like custom analysis, data logging, and protocol decoding typically require integrating BLE sniffing functionality directly into your application. The Bluetooth Framework provides this capability. The library supports the CC2540 dongle in BLE sniffing mode and includes a class that enables your application to capture all Bluetooth LE communication between devices. Should you have any questions, please do not hesitate to contact us.
How it works
The first thing you need is a CC2540-based USB Bluetooth dongle. We recommend using the CC2540EMK-USB dongle from Texas Instruments, as it ships with the required firmware pre-installed. However, you can also use any CC2540-based clone from AliExpress or other suppliers. The required firmware is available on the Texas Instruments website.
Drivers installation
Because the dongle uses a proprietary (Cebal) driver by default, you need to change it to WinUSB. This is very easy to do by following the steps below:
- Download Zadig.
- Start the Zadigapplication.
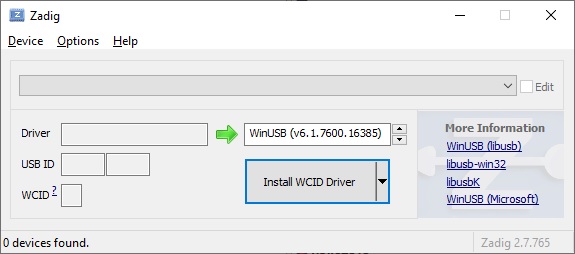
- Make sure that the List All Devices menu item is checked in the Options menu.
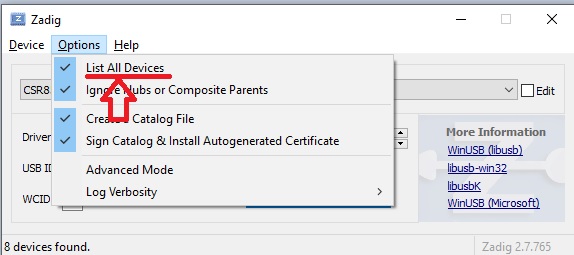
- Select CC2540 USB Dongle in the drop down list box.
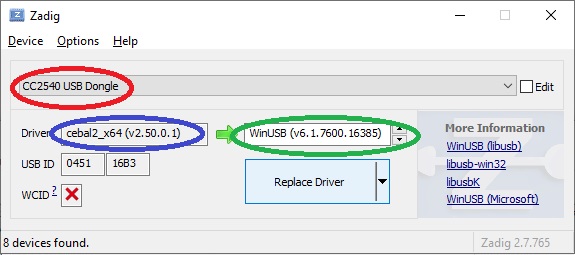
- Make sure that the source driver is Cebal.
- Make sure that the target driver is WinUSB.
- Click the Replace Driver button.
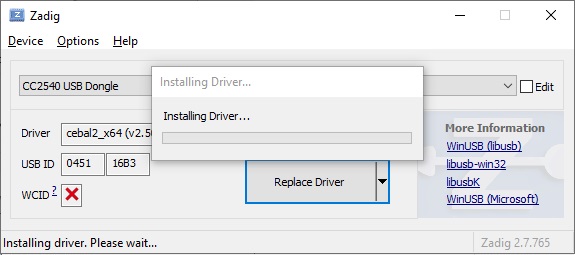
- Once driver installation finished you will see the The driver was installed successfully message.
Now all is ready to use the CC2540 USB dongle with the Bluetooth Framework to capture Bluetooth LE communications. To revert the original driver back:
- Open the Device Manager.
- Find the CC2540 USB Dongle device under the USB Devices node.
- Delete the device.
- Refrsh devices. This re-found the device and installs the original Cebal driver.
Sample application
The Bluetooth Framework includes the BleSniffer sample application, which can be used as a starting point for developing your own Bluetooth LE sniffing application and for testing the Framework's BLE sniffer solution. A BLE sniffer captures packets in two main modes (scenarios):
- Advertising mode
The dongle captures advertising packets, mainly on the primary advertising channels (37, 38, 39). In this mode, you can locate a target Bluetooth LE device and select it for capturing its communication. - Connection mode
It captures raw packet data exchanged between two Bluetooth LE devices during a connection (the remaining 37 channels: 0 through 36).
After starting the BleSniffer sample application, you need to provide the advertising channel number, which can be 37, 38, or 39. Once the capture process begins, the application will report all received BLE packets. When a connection request is captured, the sniffer automatically follows the channel changes to capture control and data frames. The Bluetooth Framework BLE sniffer can decode the following advertising PDUs:
- ADV_IND
- ADV_DIRECT_IND
- ADV_NONCONN_IND
- SCAN_REQ
- SCAN_RSP
- CONNECT_IND
- ADV_SCAN_IND
The data PDUs and any other unknown packets are reported as raw byte streams and can be decoded by your application. If you need to add any other PDUs decoding, please contact us, and we will do our best to add the required decoding. Please note that BLE packet capturing produces a high-volume data stream. Process received data frames as quickly as possible. For better performance, consider copying a captured frame and analyzing it in a separate thread. Avoid using asynchronous operations within the capture event handlers.